This op-ed was originally published in DC Journal on June 28, 2023.
Restrictive social media legislation has cropped up in states from Utah to Ohio from legislators seeking to limit teens’ screen time — or ban them from sites altogether. But if states ignore the issues presented by age-verification mechanisms, it could lead to far more dangerous outcomes for teens.
Everyone agrees teens need online protection. Parental controls and support tools that help them monitor and guide their teens’ online activity are methods worth pursuing. A litany of concerns come with legislating teen interaction on social media, the most pressing of which is the real danger posed by age-verification methods.
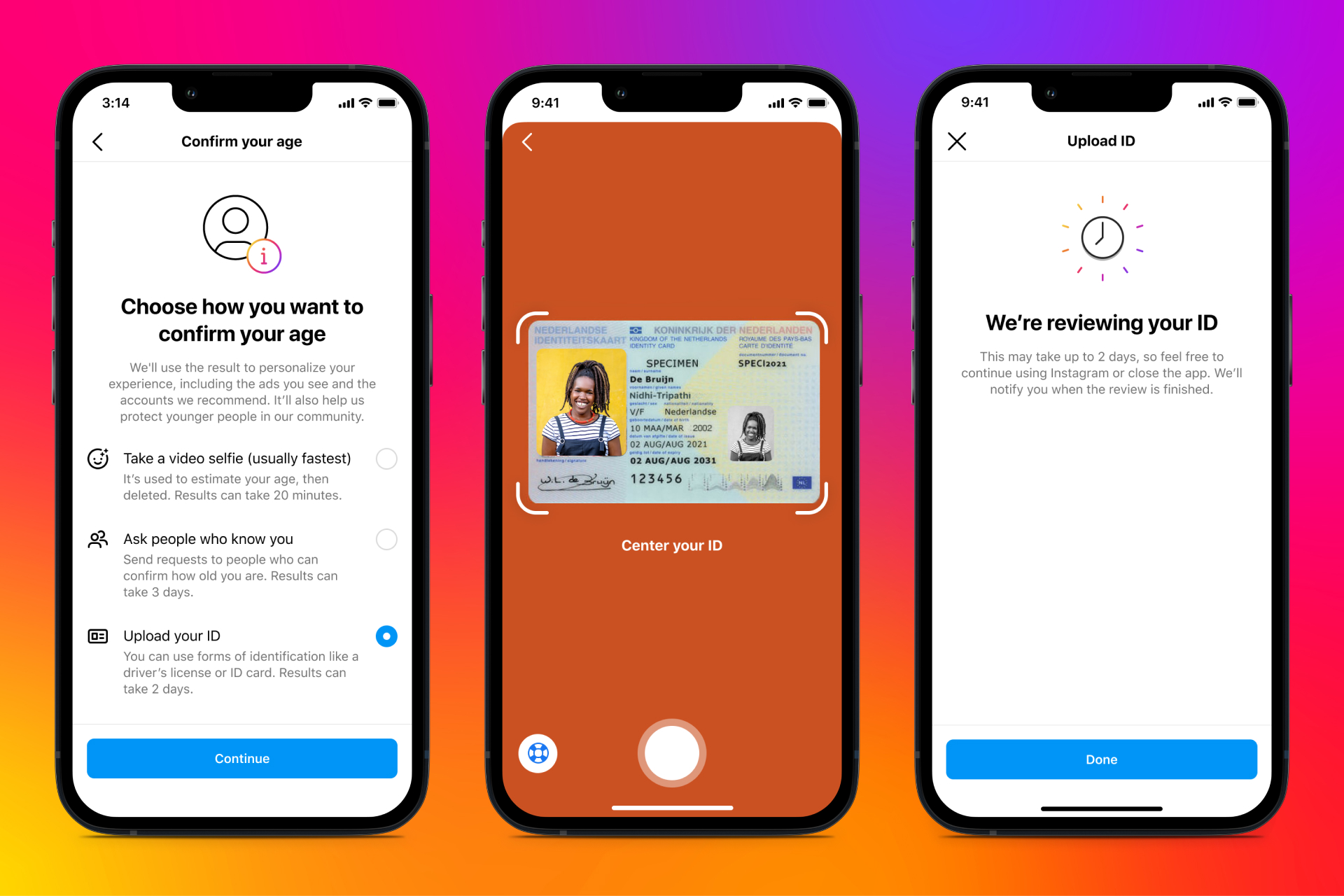
Many of these bills mandate that social media companies verify the age of users. But there are very few methods available short of requiring users to submit a driver’s license or another government ID. This practice has the potential to put sensitive personal data at risk. And the storage of that information is already being argued in court.
An equally dangerous age-verification requirement can be found in Arkansas’ law, which requires a “middleman” to verify a user’s age online. As with any internet-facing service, every new access point comes with a greater risk of vulnerability. And the middleman written into Arkansas’ law, a third-party vendor, creates a unique point of vulnerability for would-be hackers.
The Danger of Cyberattacks
In the past, some of the most significant cyberattacks were successful because of third-party vendors. Department store giant Target, for example, exposed the financial information of 110 million customers in 2013 when it gave an HVAC company access to its network. Equifax, the credit reporting agency, exposed the Social Security information of 143 million people in 2017 because of an unrenewed third-party public-key certificate. Not to mention the 2018 Cambridge Analytica scandal that cost Facebook $5 billion.
To avoid these issues, most social media companies vet their third-party vendors or build systems themselves. But under the Arkansas law, companies are forced to open up the flow of data to a third-party vendor. This requirement exposes social media companies to challenging cybersecurity threats by adding a new point of cyber vulnerability.
The Real Danger of This Law
But the kicker here isn’t that the law will expose data about a person’s favorite movie or their voting preferences. It’s going to be either a user’s government ID that contains a home address or a user’s facial scans that contain their biometric information.
A successful cyberattack on this data source would significantly harm adults, but the danger to teens is far greater. Access to minors’ sensitive information — like their home address — opens them up to risks of being stalked by predators in the real world.
Without better age-verification methods, such attacks are inevitable.
During public hearings on these bills, some proposed that a government entity, not a private third-party, is best suited to verify age. But putting aside the issue of making people obtain permission from the government to watch videos online, the state of data security within government agencies is in bad shape. In Utah, for example, a recent audit of a state agency handling people’s information shows a startling picture of practices that fall short of established privacy practices.
As more legislators take note of the online child safety laws of other states, it is crucial that they evaluate the method used to protect teens. Social media companies are already developing and implementing innovative parental controls and support tools — legislators would do well to partner with them.
But when it comes to statutory restrictions that use age-verification mechanisms, legislators should slow down. It’s impossible to contain a breach once it occurs, and that’s enough reason to get these bills right the first time with as much input as possible.